AI-Driven EDR
What AI-Driven EDR Can Do for You
To be sure your endpoints aren’t the weak link against cyber threats, it’s time to embrace the new approach to EDR, built on a strong artificial intelligence (AI) foundation and rooted in threat prevention. Are you ready for smarter EDR?
A New Approach To EDR
Get the Whole Story
When a threat is thwarted, security staff must be able to capture critical data and perform a root cause analysis to understand the origin of the attack and how an attacker attempted to compromise the endpoint.
Visibility Informs Action
If a computer behaves irregularly or it is determined that an endpoint may be at risk of compromise, an organization's security toolkit must deliver the visibility required to make definitive judgments.
Expose Hidden Threats
Take the next step, locate, and expose hidden threats where they can be mitigated. Long considered a task for elite security analysts, AI-driven EDR simplifies the process, making it available to every member of your security team.
Automate Threat Detection
To root out threats before they can cause serious damage, an automated approach to threat detection that combines static, machine learning, and custom rules is required to identify and block advanced threats.
Traditional EDR vs. AI-Driven EDR: A Comparison
| Traditional EDR | CylanceOPTICS™ | Benefits | |
|---|---|---|---|
Security Approach |
Provides reactive detection and response | Provides continuous threat and incident prevention | A prevention-based approach reduces the overall number of incidents that require action/analysis |
Required Skills |
Requires advanced security analyst skillset | Is built for security analysts of all skills and experience levels | A solution accessible to all widens the pool of possible talent who can manage the solution |
Data Collected |
Streams all endpoint activity to the cloud continuously or sends it to dedicated hardware | Collects and stores only security-relevant data locally | Collecting only security-relevant activity data locally significantly reduces liability and improves compliance |
Data Storage |
Continuously streams data to the cloud or aggregates on local hardware | Stores data locally on each endpoint | Storing data locally significantly reduces liability, improves compliance, and optimizes performance and scalability |
Threat Detection Techniques |
Requires individual behavior rules be written and continually augmented to maintain coverage levels running from the cloud | Combines behavior rules with trained ML threat detection modules to provide a greater - and always increasing - breadth of coverage, running locally on the endpoint | Eliminates the need for up to thousands of rules that must be created and maintained by a security expert |
Threat Hunting |
Requires significant expertise to configure and perform a multitude of search capabilities | Provides easy to configure search criteria and optimized collection of responsive data from endpoints | Increases ability to uncover hard-to-find threats without adding sta |
Root Cause Analysis |
Combs through collected data to determine where an active threat entered the environment to determine how to stop ongoing damage | Uses data collected when the threat is prevented by CylancePROTECT to understand the attack vector chosen by the bad actor | Automated approach shortens time to analysis completion |
IR Capabilities |
Requires extensive security expertise to use the advanced tools that identify and mitigate security issues | Takes automated IR actions or enables manual action, deploying pre-configured and custom response actions to return the system to a trusted state quickly | Automation and machine learning allow organizations big and small to maintain the security posture once thought only available to the largest of organizations |
Expanding Machine Learning Applications on the Endpoint
Endpoint detection and response plays a key role in enterprise security, but not all EDR solutions are created equal. According to 451 Research, "as organizations look to deploy or improve their EDR practices, they should consider the possible applications of machine learning approaches."
Extend and Augment Your Security Strategy with Cylance Consulting
While CylanceOPTICS automates the threat detection and response processes, Cylance’s consulting team of experts can help you identify and mitigate threats even faster with fewer resources, while our ThreatZERO white-glove service offers dedicated support for all of our solutions.
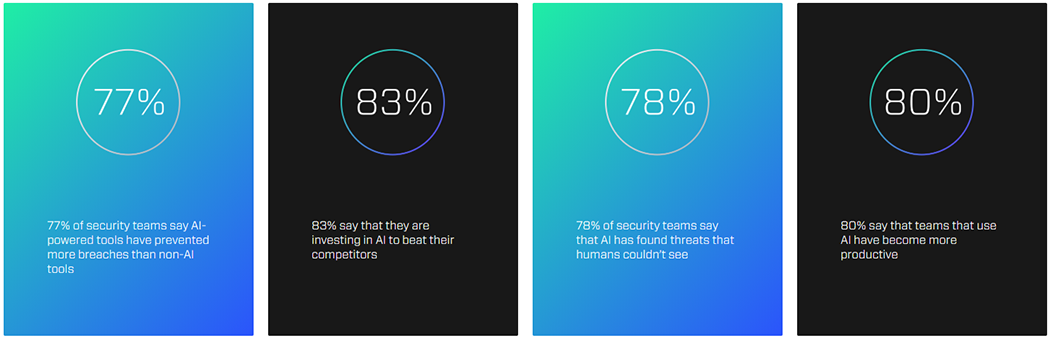
Don't Take Our Word for It
C-suite and IT professionals across every industry are looking to AI to bolster security at their enterprise.