
BlackBerry Cylance CylanceOPTICS
AI-Powered Endpoint Detection and Response

Price per endpoints. Quantity must be 100 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 251 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 501 or greater
Our Price: Request a Quote
Click here to jump to more pricing!
Please Note: All Prices are Inclusive of GST
 Overview:
Overview:
Prevent. Detect. Respond. CylanceOPTICS pushes all detection and response decisions down to the endpoint, eliminating response latency that can mean the difference between a minor security event and a widespread, uncontrolled security incident.
CylanceOPTICS is an endpoint detection and response (EDR) solution that extends the threat prevention delivered by CylancePROTECT using artificial intelligence (AI) to identify and prevent widespread security incidents.
CylanceOPTICS provides:
- AI-driven incident prevention
- Context-driven threat detection
- Machine learning threat identification
- Root cause analysis
- Smart threat hunting
- Automated remote investigations
- Dynamic playbook-driven response capabilities
Due to the evolution of the threat landscape and the continuous expansion of the attack surface, organizations are challenged to maintain a situational awareness and a steady-state security posture. Advancements in security technology have helped make it more difficult for attackers to be successful, however, organizations face two challenges that show no signs of lessening:
- Skilled security expert shortage: With a shortage forecasted to be in the millions within the next five to 10 years, organizations will find it more difficult to add skilled resources to their team, not to mention maintain their current team makeup. Therefore, organizations are seeking out security solutions that combine advanced security capabilities with automation that allow them to mitigate the risk of this human resource shortage.
- The need for security purchases to show positive return on investment (ROI): Despite the increased visibility into debilitating outbreaks, security team management often find themselves fighting for security budget. Often security management must agree to demonstrate a reasonable ROI to have budget released. Therefore, now more than ever, organizations are seeking out security solutions that offer the opportunity for threat reduction while simultaneously providing demonstrable ROI.
The Winter release of CylanceOPTICS delivers new detection, investigation, response, and automation capabilities that enable organizations concerned with advanced threats, delivering ROI, and staffing issues to adopt an EDR solution with ease.
The Case for Prevention First Security
Prevention products that rely on signatures cannot keep pace with today’s fast-changing attacks, leaving security teams wading through a sea of alerts daily. Finding the critical security issues is near impossible, leaving attackers to run rampant across the business.
Prevention-first security can significantly reduce the number of alerts generated by the security stack, decreasing the burden and frustration associated with endless alert investigations that lead nowhere.
With CylancePROTECT preventing malware, malicious scripts, rogue applications, and fileless attacks from harming the business, CylanceOPTICS provides the AI-powered EDR capabilities required to keep data and businesses secure.
CylanceOPTICS is an EDR solution designed to extend the threat prevention delivered by CylancePROTECT by using AI to identify and prevent security incidents.
Unlike other EDR products that are difficult to deploy, hard to maintain, and even harder to use, CylanceOPTICS:
- Can be installed on any endpoint in minutes with no hardware or expensive data streaming required
- Enables zero-latency detection and response by storing and analyzing data locally on the endpoint without needing constant updates
- Delivers self-contained, automated, machine learning threat detection modules designed to uncover threats that would be difficult to find with static behavior rules
CylanceOPTICS, working with CylancePROTECT, delivers the detection and prevention capabilities needed to stay ahead of the attackers, keeping the business secure.
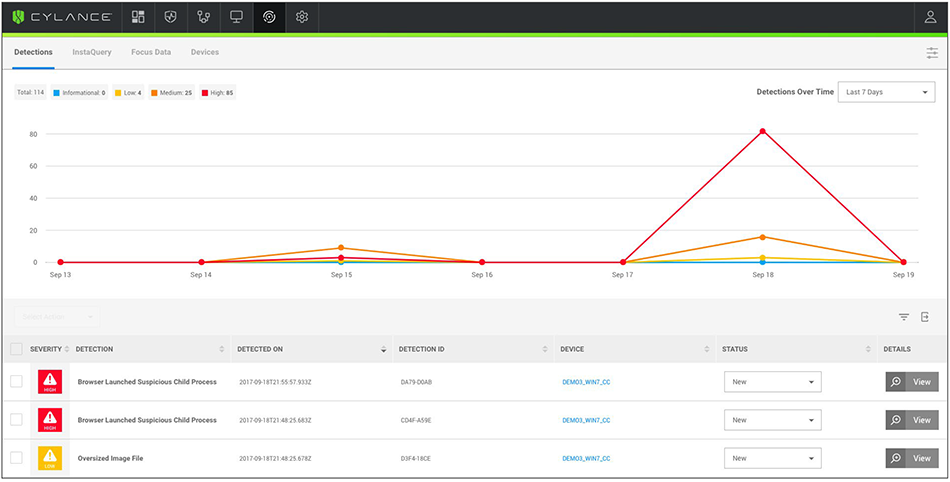
Detections tab displays event trends over time with access to detailed threat information.
The Power of CylanceOPTICS
The power of CylanceOPTICS comes from the unique and efficient way threat detection and response capabilities are delivered. Unlike other EDR products that rely on cloud-based analysis to uncover threats and security analysts for response, CylanceOPTICS pushes all detection and response decisions down to the endpoint, eliminating response latency that can mean the difference between a minor security event and a widespread, uncontrolled security incident.
Each rule, whether default, custom, or machine learning, can be configured with a playbook that can initiate a set of discrete response tasks automatically if the rule is triggered. The playbook-driven response capabilities assist organizations in eliminating dwell time by ensuring threat responses are fast and consistent across the environment regardless of the skill-level of the on-duty security personnel.
CylanceOPTICS also includes remote investigation capabilities that make completing detailed incident analysis fast. Analysts can quickly deploy packages to endpoints to collect critical artifacts as well as complete other tasks, even using other tools remotely, drastically reducing the time to resolution.
CylanceOPTICS allows security analysts to dissect any CylancePROTECT-prevented attack to determine root cause to improve their overall security framework. CylanceOPTICS also provides enterprise-wide threat hunting capabilities powered by InstaQuery (IQ), enabling on-demand threat hunting with instant access to the results.
Finally, CylanceOPTICS is 100% API accessible, enabling security teams to gain the benefits of AI-driven EDR without learning a new user interface. With simple-toconfigure API calls, analysts can do anything from consume threat data to perform system-wide threat hunts without ever touching the CylanceOPTICS user interface.
The threat detection, investigation, response, and automation delivered by CylanceOPTICS means organizations can maintain continuous situational awareness and strong security posture regardless of changes to the threat landscape, budget, or their security team.
| Cylance Solution | Customer Benefit |
|---|---|
| Combine static, machine learning, and custom rules to identify and block advanced threats | Organizations can reduce dwell time and the impacts of potential breaches |
| Automate investigation and response with playbook-driven workflows, ensuring appropriate actions are always taken | Organizations can drive consistent levels of security no matter the security staff skill-level |
| Implement an AI-driven preventionfirst approach to EDR through which most attacks are thwarted before they have an opportunity to execute | Organizations can save significant time and money associated with recovering from a successful attack |
Features:
AI-Driven Incident Prevention
Uncover threats that would be difficult to identify with behavior rules using machine learning threat detection modules.
Enterprise-Wide Threat Hunting
Easily search endpoint data for suspicious/malicious activity to uncover hidden threats.
Consistent Cross-Platform Visibility
Detect and prevent incidents across Microsoft Windows and Apple MacOS platforms.
Dynamic Threat Detection
Automate threat detection, in real time, using custom and curated behavior rules running on the endpoint.
On-Demand Root Cause Analysis
Understand how attacks entered the environment so corrective actions can be taken, reducing the attack surface.
Automated, Fast Response
Customize automated response actions to minimize the risk of a widespread incident.
Benefits:
- Reduce Alert Volume
Reduce security alert volume with full-spectrum threat and incident prevention, improving team efficiency - Gain Situational Awareness
Understand the attack surface across the environment, eliminating potential weaknesses - Relieve the Strain on Security Teams
Automate responses to identified threats 24x7, without disrupting the security team - Improved Threat Visibility though Syslog Integration
CylanceOPTICS now outputs all detection events to the syslog, allowing users to make use of this critical threat data across their security and IT stack. - Programmatically integrate CylanceOPTICS into the security stack with new API support
CylanceOPTICS is now fully accessible via APIs, allowing organizations to incorporate this AI-driven EDR solution into their existing management consoles without the need to use the CylanceOPTICS user interface. - MITRE ATT&CK Framework rules packages
The Cylance Context Analysis Engine, the driving force behind threat detection and response, now comes with a pre-configured set of rules mapped to the MITRE ATT&CK Framework, improving threat detection capabilities. - Reduce dwell time and increase response time and consistency with playbookdriven response
Initiate a set of discrete response tasks automatically if the rule is triggered. Playbook-driven response capabilities assist organizations in eliminating dwell time by ensuring threat responses are fast and consistent across the environment regardless of the skill-level of on-duty security personnel. - Complete suspicious device investigations faster with partial lockdown
Extending current lockdown response capabilities in CylanceOPTICS, partial lockdown will enable a security analyst to maintain communication with a suspected compromised endpoint without risk of further environment contamination.
Use Cases:
- Prevent Malicious Activity
CylancePROTECT, which provides the foundation for CylanceOPTICS, is designed to specifically prevent successful attacks aimed at endpoints. - Investigate Attack and Alert Data
Users can investigate alerts from other security controls, including CylancePROTECT, with easy to understand visualizations of all activities associated with the alert, retrieving useful information from the endpoint. - Hunt for Threats Across the Enterprise
Users can quickly search for files, executables, hash values, and other indicators of compromise across the entirety of their network endpoints to uncover hidden threats. - Endpoint Threat Detection
Suspicious behaviors and other indicators of potential compromise on endpoints will be uncovered automatically. - Rapid, Automated Incident Response
Users can retrieve critical forensic information from impacted endpoints, as well as take aggressive containment actions when a harmful endpoint is discovered. The solutions also can automatically trigger response actions if a pre-defined rule is triggered.
CylanceOPTICS Data Collection Approach:
CylanceOPTICS takes a targeted approach to data collection, capturing changes to endpoints and servers that would indicate a potential security threat.
Unlike other products that stream all changes to the cloud continuously, CylanceOPTICS stores this security-relevant data locally on the endpoint to enable fast, local decisions, minimizing response latency.
Endpoint Data Collected
| Event Type | Description of Events |
|---|---|
| CylancePROTECT |
|
| File |
|
| Process |
|
| Network |
|
| Registry |
|
| User |
|
| Removable Media |
|
Cracking the EDR Code with AI:
The threat detection, investigation, response, and automation delivered by CylanceOPTICS means organizations can maintain continuous situational awareness and strong security posture regardless of changes to the threat landscape, budget, or their security team.

Solutions:
Cylance Prevention-First Security with CylancePROTECT and CylanceOPTICS
AI-Powered Threat and Incident Prevention, Detection, and Response
Simplifying the endpoint security stack can make any security team’s work easier, and their efforts far more efficient. The challenge, however, is figuring out a way to transition to a simpler approach without impacting the organization’s security posture.
Cylance helps organizations make this change by delivering a prevention-first endpoint security solution designed to prevent successful attacks while simultaneously reducing the noise generated by the entire security stack.
With CylancePROTECT and CylanceOPTICS, organizations get artificial intelligence (AI) driven threat prevention, detection, and response. Built from the ground up to easily scale with the business, Cylance’s solutions provide innovative security that delivers real benefits to organizations.
| Cylance Solutions | Organization Benefit |
|---|---|
| Use AI to identify and block malicious applications, even those never seen before, from executing on endpoints | Organizations can dramatically decrease the likelihood that business is impacted by a zero-day attack |
| Combining static, machine learning, and custom rules to identify and block advanced threats | Organizations can reduce dwell time and impacts of potential breaches |
| Automate investigation and response with playbook-driven workflows, ensuring appropriate actions are always taken | Organizations can drive consistent levels of security no matter the security staff skill-level |
| AI-driven prevention-first approach to EDR through which most attacks are thwarted before they have an opportunity to execute | Organizations can save significant time and money associated with recovering from a successful attack |
Capabilities at a Glance
CylancePROTECT
- AI-driven malware prevention
- Memory exploitation prevention
- Device policy enforcement
- Script management
- Application control for fixed-function devices
CylanceOPTICS
- Context-driven threat detection
- On-demand root cause analysis
- Enterprise-wide threat hunting
- Automated playbookdriven response
- Remote investigation and remediation
Meeting Your Security Requirements - Use Case Summary
The following are examples of common security use cases that Cylance’s prevention-first security solutions addresses:
Prevent Successful Attacks
Malware (Ransomware, Trojans, Adware, Etc.)
The best way to protect endpoints from attackers is to identify and stop the attack before it ever starts. Cylance solutions use field-proven AI to inspect portable executable files attempting to run on an endpoint before it executes. Within milliseconds, the machine learning model running on the endpoint determines if the executable is malicious or safe. If malicious, the executable is prevented from running, thwarting the attacker’s attempt to compromise the endpoint.
Fileless Malware
Fileless attacks are on the rise as attackers realize the ease with which legitimate admin tools and memory can be used to compromise a system without writing any files to the disk. Many security products have no ability to prevent these types of attacks, but with Cylance solutions, memory exploit prevention, script management, and the fileless threat detection modules block these attacks before they have a chance to impact the business. When an attacker attempts to escalate privileges, undertake process injection, or make use of an endpoint’s memory inappropriately by other means, Cylance solutions will detect and prevent it immediately.
Malicious Scripts
Scripts are a favorite tool of choice for many attackers for several reasons. First, for novice attackers, malicious scripts are readily available in the cyber crime underworld, which makes it easy to find one that meets the attacker’s needs. Additionally, scripts are often difficult for security products to detect, as there are many legitimate uses for scripts. With Cylance solutions, organizations get built-in script management, meaning security professionals maintain full control of when and where scripts are run in their environment, reducing the chances that an attacker can use this attack vector to cause harm to the business while still allowing their legitimate use.
Malicious Email Attachments
Phishing attacks are one of the most effective ways attackers gain access to an endpoint. Employees unwittingly open malicious attachments, thinking they are legitimate, and enable attackers to undertake any number of malicious actions. With Cylance solutions, weaponized attachments are identified and blocked automatically. If a document, for example, includes a VBA macro deemed to be risky, it will be blocked from executing. This protection adds an additional layer of security, protecting employees from becoming the victim of an attacker and introducing a compromise to the environment.
External Devices
USB devices are littered across most organizations. Most of these devices are useful tools, enabling employees to share files with others quickly and efficiently. However, these devices can cause significant damage to environments if they are loaded with malware or are used to transfer sensitive data outside of the business. To combat this risk, Cylance solutions have built-in device usage policy enforcement. This capability allows administrators to control which devices can be used in their environment. This ultimate control limits the chance that an external device enables an attacker to successfully execute an attack or exfiltrate data.
Investigate Attack and Alert Data
Perform Root Cause Analysis and Data
Collection To Determine the Origin of the Attack Stopping a threat from impacting endpoints is critical to ensuring sensitive data remains secure. Going one step further, when a threat is thwarted, critical data is captured so security professionals can see how an attacker attempted to compromise the endpoint. Cylance solutions deliver this capability, not only for blocked attacks, but for any potential threat that may be found on endpoints. With a simple click, the timeline of activities that led up to the threat, known as a Focus View, can be generated. Additionally, data can be remotely collected from the impacted endpoint to gain further insight into the attempted attack or suspicious activity. This provides an understanding of how the attacker attempted to exploit the environment, so steps can be taken to ensure any vulnerability or gap in security controls can be addressed.
Perform Targeted Threat Hunting
Uncover Hidden Threats
Some malicious activities are easy to identify, while others are anything but cut and dry. When a computer begins to behave irregularly, or it is determined that an endpoint may be at risk of compromise, it is critical that an organization’s security toolkit gives it the visibility required to make definitive judgments. Cylance solutions provide immediate access to the forensically-relevant data stored on any endpoint. Within moments of a suspicious activity being identified, searches can be targeted to the exact threat being investigated.
Use Indicators of Compromise To Find Threats
Threat hunting can be described as the act of forming a hypothesis and then running a series of searches/ investigations, using IOCs or other terms, to either prove or disprove that hypothesis. Having access to the right data is at the essential core of performing this skill effectively. Targeted threat hunting with refined results is capable with Cylance solutions, delivering access to both current and historical endpoint data. Unlike other tools that store every piece of data from an endpoint, Cylance solutions store only the forensically-relevant data, meaning security teams won’t have to spend time sifting through mountains of irrelevant information to find threats.
Context-Driven Threat Detection
Static, Machine Learning, and Custom Rules
There are several ways to identify potential threats and compromises. First, security analysts can perform searches across endpoints to identify suspicious artifacts, and through manual investigation, determine that a threat exists. While there is tremendous value in this process, it simply does not scale across an enterprise. To root out threats hidden on endpoints, an automated approach to threat detection must be used. The power of CylanceOPTICS comes from the unique and efficient way threat detection and response capabilities are delivered. Unlike other EDR products that rely on cloud-based analysis to uncover threats and security analysts for response, CylanceOPTICS pushes all detection and response decisions down to the endpoint, eliminating response latency that can mean the difference between a minor security event and a widespread, uncontrolled security incident. The Context Analysis Engine, the driving force behind CylanceOPTICS threat detection and response, enables security analysts to choose from a wide variety of default detection rules developed by Cylance security specialists, including a package of rules that map to the MITRE ATT&CK Framework, or create their own custom rules that meet specific business needs. Analysts can also choose to deploy machine learning threat detection rules to the endpoints to uncover threats that would be difficult, if not impossible, to uncover with static rules.
Take Response Actions
Even with security controls in place, no business can guarantee that every single attack can be stopped. This means organizations must be prepared to respond when an attack is detected. With Cylance solutions, enterprises get fully-integrated automated incident response capabilities. Each rule, whether static, machine learning, or custom, can be configured with a playbook to initiate a set of discrete response tasks automatically if the rule is triggered. The playbook-driven response capabilities assist organizations in eliminating dwell time by ensuring threat responses are fast and consistent across the environment regardless of the skill-level of the on-duty security personnel. If an attack is detected, a response can be initiated automatically, with no human intervention. If further responses are required, the item in question can be quarantined and the endpoint can be locked down, disabling its ability to communicate with any other endpoints. Forensic data from the impacted endpoint can be collected to gain further context about the incident. Identifying a security concern is important, but having the ability to respond automatically is a necessity. With Cylance solutions, organizations have that ability. True endpoint security does not come from prevention or detection. To combat today’s attacks, organizations must have strong prevention and detection capabilities in place to keep pace with attackers. With Cylance solutions, enterprises get the best of both worlds, maximizing the return on security stack investments, making analysts more efficient, and making the business more secure.
CylanceAPI:
Scalable, Repeatable, and Automated Workflow Integration
CylanceAPI is a series of RESTful APIs that deliver easy access to CylancePROTECT data, administration, and investigation tasks to enable full integration of CylancePROTECT into an existing security framework and workflows. Unlike other security product integration frameworks that require extensive coding expertise, CylanceAPI allows anyone to use CylancePROTECT data without being an expert programmer. With straightforward data structures and the ability to test integrations easily, CylanceAPI sets the standard for smooth product integration.
For CylancePROTECT customers, CylanceAPI allows security teams to easily automate recurring tasks such as adding new devices to the environment and performing routine security operations.
Cylance technical partners can make use of the CylanceAPI framework to integrate CylancePROTECT into other third-party tools such as orchestration and case management products.
The following APIs are available within CylanceAPI:
- Tenant User: Reporting, creation, and management of tenant uses (user, zone manager, and admin)
- Device: Reporting and management of devices belonging to a tenant
- Zone: Creation and management of zones belonging to a tenant
- Policy: Creation and management of device policies belonging to a tenant
- Threat: Reporting and management of threat events detected by CylancePROTECT
- Global List: Management of the Global Safe List and the Global Quarantine List within a tenant
Common Use Cases
The following uses cases are supported by CylanceAPI:
- Bulk Actions
- Move devices from one zone to another
- Update policy for multiple devices
- Add policy-level exclusions
- Reporting
- Device health and summary
- Threat overview
- Device Grouping and Management
- Zone creation
- Auto device-zone assignment
- Activity Response
- Add new files to global safelist and quarantine lists
- Waive and quarantine incoming threats
- Event Correlation
- Integrate CylancePROTECT data with other security tool data
- Improve the ability to identify advanced threats
CylanceAPI Benefits
For Cylance Customers
Use the rich CylancePROTECT data to improve security posture
- Use CylancePROTECT threat data in other security tools in the environment
- Correlate threat data to further understand the attack surface
- Improve situational awareness across the security team
For Cylance Technical Partners
Automate common tasks to improve IT and security team efficiency
- Reduce the time and potential errors associated with common IT tasks such as adding devices to the environment
- Drive consistency across the IT and security team
- React quickly and apply changes quickly across the environment
Documentation:
Download the BlackBerry Cylance CylanceOPTICS Datasheet (.PDF)
Download the BlackBerry Cylance What's New in CylanceOPTICS Datasheet (.PDF)
Download the BlackBerry Cylance CylanceOPTICS Solution Brief (.PDF)
Download the BlackBerry Cylance CylanceAPI Datasheet (.PDF)
Pricing Notes:
- All Prices are Inclusive of GST
- Pricing and product availability subject to change without notice.
Price per endpoints. Quantity must be 100 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 251 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 501 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 1,001 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 2,501 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 5,001 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 1 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 100 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 251 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 501 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 1,001 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 2,501 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 5,001 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 1 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 100 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 251 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 501 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 1,001 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 2,501 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 5,001 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 1 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 100 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 251 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 501 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 1,001 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 2,501 or greater
Our Price: Request a Quote
Price per endpoints. Quantity must be 5,001 or greater
Our Price: Request a Quote

