
Incident Response and Containment
Eliminate Operations and Critical Asset Risks
Eliminating ICS Vulnerabilities. Industrial Control Systems (ICS) are targeted by the same cybersecurity threats that corporate networks face. Our team employs passive and non-invasive techniques to identify, improve, and optimize the security posture of highly-sensitive systems.
Why Choose Cylance Consulting for ICS?
Adaptive to Each Client and Industry
We review all components to provide a comprehensive solution, then implement a system friendly methodology, testing component vulnerabilities in a lab setting to avoid the risks associated with software agents and network scanning of critical infrastructure.
Balance Risk With ROI
A state of prevention is an investment. Cylance Consulting looks at variables, weighs business impact, finds ways to prioritize risk mitigation strategies, and identifies quick wins that immediately improve your security posture while also potentially reducing costs.
Prevent Attacker Access and Movement
Cyber criminals are looking for their next opportunity. Our prevention-first methodologies leverage AI to stop attacks before they happen. We reduce the attack surface, identify vulnerabilities, and look for indicators of compromise within the control system environment.
Systematic. Repeatable. Secure.
Your organization deserves detailed, easy-to-follow procedures customized to your individual environment and personnel. We work with you to design and deploy solutions plus provide the training necessary to maintain a top-level security workforce.
Keep Critical Environments Operational
ICS Security Assessment
Cylance experts identify the highest priority security concerns, evaluated against potential business risk, and quickly provide recommendations. The resulting risk profile is part of your roadmap for prioritizing and remediating vulnerabilities that need to be addressed.
Building Automation Assessment
Cylance Consulting helps organizations identify and remediate vulnerabilities that pose a risk to IT and OT networks…and potentially impact the functioning of your smart building HVAC, fire suppression, electronic security, smart lighting, or elevators systems.
ICS Security Monitoring
Cylance ICS Security Monitoring provides owners and operators with greater visibility into mission-critical devices and equipment. We do this by helping you align business-critical assets and operations with the accessibility of network activity and device logs.
ICS Security Fundamentals
Cylance ICS security experts work closely with you to assist in the implementation and integration of foundational Industrial Control System security best practices. Whether reviewing a design, assisting with vendor selection or building a validation plan, we will help fulfill your needs and protect your organization.
ICS Policy Gap Analysis
Building a comprehensive cybersecurity policy helps minimize exposure to risk and ensures a clear strategy for handling incidents and continually improving/monitoring the environment. Gap analysis can determine how you align with NIST CSF and industry best practices.
ICS Security Assessment:
Identify and Mitigate Risks in ICS Environments
Industrial Control Systems (ICS) manage an organization’s risk, including security. While ICS were once stand-alone systems, they are now connected to an organization’s IT infrastructure, yet contain fewer security controls. ICS now faces the same cybersecurity threats as corporate networks, but with cascading risk, physical damage, and bodily injury as potential impacts.
Additional challenges remain, such as applying patches vs. system downtime, an ICS system whose patches are at end of life, and dependencies on other systems with heterogeneous environments. All of these challenges make upgrades and updates challenging. Recent attacks, including NotPetya, Wannacry, Shamoon 2, BlackEnergy, Havex, and Clear Energy, demonstrate that attacks need not be targeted. A lot of work remains to protect vital systems and avoid business interruption and theft of data.
Further, it is also critical that organizations look into the security of their large, connected supply chains. Small companies providing critical components can also be targeted by threat actors and present cascading risks to the integrity of an organization’s production process. With the OT team looking after the integrity of production process and the IT team after data protection, traditional trade-off between uptime/safety and security functionality (both perceived and real) continue.
Because of these unique challenges, ICS operators are left scrambling with IT and OT segmentation efforts, random uses of off-the-shelf security technologies such as antivirus, firewalls, etc., and some patching that is usually limited to Windows systems (servers and workstations). As significant production and financial losses are tied to any disruption in ICS, strengthening and securing an ICS environment has become more important than ever before.
While many considerations must be taken when addressing the fragile nature of ICS environments, an ICS Security Assessment can aid in identifying and remediating vulnerabilities that would allow an attacker to disrupt or take control of the system. Based on the results, the assessment can help guide decisions on corporate best practices to enhance the organization’s overall cybersecurity posture.
Benefits
- Increase comprehension of cybersecurity in industrial control systems, including best practices for securing ICS with integrated IT/OT systems
- Develop a systematic and repeatable approach to assessing and maintaining the security posture of ICS systems, including legacy architectures, legacy systems, and legacy devices, without replacement
- Support business objectives while maintaining safe and uninterrupted operations with security
- Create remediation strategies while balancing risk and return
- Implement a prevention-first methodology that removes the noise in environments and allows IT security professionals to focus on the activities that can be truly harmful
Service Overview
Cylance Consulting’s globally-recognized ICS security experts will work closely with organizations to evaluate the security practices of the ICS environment and understand the challenges from their perspective. These security challenges are mapped on a timeline to illustrate key milestones and to identify any additional measures that need to be taken to improve the client’s security over six to 24 months. Apart from these holistic assessments and project roadmap, Cylance’s ICS experts also provide clients with metrics to report progress and a measured approach to improve capabilities to detect/respond to threats.
Cylance’s approach is centered on providing context with regard to the potential business impact of cyber threats. By applying a structured and methodical approach to security, Cylance ICS experts will map out the different types of threat actors, their potential entry points, detection points, as well as prevention and containment opportunities within the network. This will help clients better understand the robust security tools they have in place and any countermeasures that need to be implemented.
Service Offerings
An ICS Assessment provides an effective means to identify the highest priority security concerns and recommendations for the control system environment. Information is collected about the organization’s security practices, policies, and procedures through survey responses, staff interviews, tools, company documentation, and site walk downs. The primary categories for the assessment include:
ICS Security Assessment and Strategic Roadmap
A range of assessment activities focused on analyzing the effectiveness of an organization’s security programs, this service looks into vulnerabilities and solutions to mitigate their critical risks/impacts. The strategic roadmap helps organizations build and prioritize the governance and remediation of critical vulnerabilities surrounding people, processes, and technologies.
ICS Risk Assessment
A high-level assessment focused on analyzing the overall posture and strategic direction of an organization, this service additionally supports a peer analysis across multiple owned assets.
ICS Security Testing
Designed to help organizations evaluate specifically implemented technologies or security controls, this service covers traditional IT, embedded devices, operations technology, control systems, and more.
ICS Security Response and Readiness
A range of assessment activities focused on analyzing an organization’s readiness to respond to security incidents within their ICS, this service covers people, processes, and technology challenges in detection, response, and recovery around ICS assets.
The Cylance Difference
Holistic IT and OT Coverage
Cylance has ICS experts that have a wide range of expertise covering both IT and OT capabilities, allowing them to balance the concerns of both sides and ensure that they are aligned, integrated, and consistent. Cylance works closely with organizations to discuss ways to protect legacy architectures, legacy systems with outdated operating systems, and legacy devices, and ways to prevent malicious threat actors from shutting down your grid and halting your business operations.
No Business Interruption
Cylance performs any service activity without interruption to operations. From assessments to roadmap review to the execution of remediation efforts, Cylance’s objective-based approach always looks at the protection of critical business operations and systems.
Prevention-first Methodology
Cylance leverages AI and a prevention-first methodology to secure endpoints from both known and unknown attacks. Cylance’s prevention-first strategy utilizes an adversarialbased approach for hygiene to quickly identify threats from commodity malware to sophisticated threat capabilities. Removing the noise from environments allows IT security professionals to focus on the activities that can be truly harmful.
Flexible Planning
Cylance Consulting works with cyber insurance carriers, law firms, OT, security teams, and risk managers to identify the highest priority concerns and provide the recommended order for improvement. While not all organizations will be able to implement security best practices all at once, Cylance balances projects against budget to help clients achieve their roadmap goals.
Deliverables
The information obtained from the assessment is used to provide the organization with:
- A risk profile that addresses impact, threat, vulnerability, probability, and countermeasures
- A prioritized road map for remediating security concerns
Identify weaknesses and develop actionable recommendations to mitigate the risks in your ICS environment. Contact Cylance Consulting or your technology provider to discuss your needs.
Other Related Services
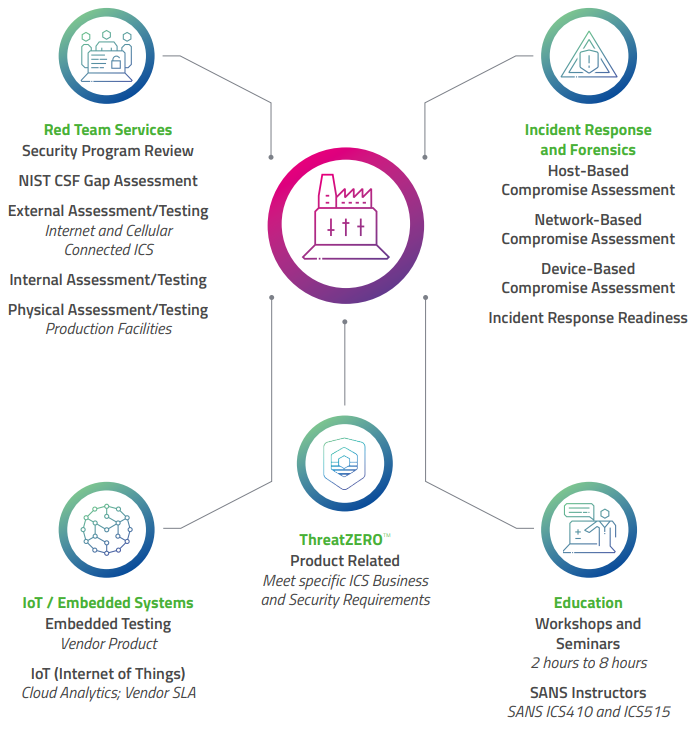
Cylance’s experts are world-renowned and have vast experience in working synergistically across various practice areas. They deliver consistent, fast, and effective services across the globe. Cylance’s ICS Assessment can be integrated with other Cylance services around Incident Containment and Compromise Assessments, Red Team Services, IoT and Embedded Systems, and ThreatZERO™ Services.
Download the Cylance ICS Assessment Datasheet (.PDF)
Building Automation Assessment:
Identify and Mitigate Risks in Your Smart Building
Today, cybersecurity protection and risk prevention for building automation systems (BAS) and building management systems (BMS) are a necessity. The operational, financial, and reputational impact to a business is tremendous and can include lockedout systems, fire suppression/lighting/HVAC failures, introduction of malicious files into the corporate network, and overall interruption of business and operations. An organization’s IT and facilities departments must collaborate to close potential attack avenues.
Cylance Consulting’s Building Automation Assessment helps organizations identify and remediate vulnerabilities that pose risk to the IT and OT networks and could impact the function of the smart building.
Benefits
- Identify processes, systems, and technologies involved in integrated buildings and IT systems
- Understand the types of cyberattacks which may be targeted at intelligent buildings
- Identify and evaluate threat sources
- Understand the roles, responsibilities, and capabilities of various stakeholders, including building systems vendors, IT personnel, and system integrators
Service Overview
Cylance Consulting’s ICS security experts will work closely with organizations to evaluate the security practices of building automation systems. Multiple systems including HVAC, fire suppression, electronic security systems, and smart lighting controls are analyzed against known and potential vulnerabilities as well as operational dependencies.
The assessment provides context related to the potential business impact of cyberthreats, the vulnerability of the systems to attack, and whether there are any current indicators of compromise. It provides an effective means to identify the highest priority security concerns and recommendations for securing the environment.
Information is collected about the organization’s security practices, policies, and procedures through survey responses, staff interviews, tools, company documentation, and site walk downs.
Deliverables
The information obtained from the Building Automation Assessment is used to provide the organization with:
- A risk profile that addresses impact, threat, vulnerability, probability, and countermeasures
- A prioritized road map for remediating security concerns
Cyber-related issues play an increasing role within building networks and it is important to take an active role in managing risk. Contact Cylance Consulting or your technology provider to discuss your needs.
Download the Cylance Building Automation Assessment Datasheet (.PDF)
ICS Security Monitoring:
Detect Malicious Activity on Critical Infrastructure
The convergence of information technology (IT) into operational technology (OT) has resulted in significant cybersecurity risk, threatening the reliability of control systems. The importance of network security monitoring of industrial control systems (ICS) cannot be understated. The stakes are too high for complacency or inattention.
ICS Security Monitoring from Cylance Consulting not only helps organizations identify and stop cybersecurity threats, but also provides owners and operators with greater visibility into the performance of their mission-critical devices and equipment.
Benefits
- Gain real-time visibility into all devices communicating on your ICS network
- Establish an accurate baseline of communications to proactively address threats to reliability and cybersecurity
- Identify the source and intent of unusual activity on the ICS network
- Identify everything that has been changed, patched, or upgraded throughout its entire lifecycle for more reliable operations and maintenance
- Mitigate malicious behavior early, thwarting significant financial and physical damage
Service Overview
Cylance Consulting ICS experts understand that network security monitoring is a way to find intruders on your network, enabling you to respond to them before they cause damage to your enterprise. Leveraging Cylance Consulting’s knowledge of traffic and data flows allows your organization to build a baseline of ‘normal’ operation. In addition to cybersecurity, this helps control engineers to detect deviances in key processes to recognize poorly performing equipment and processes that have, or are in the process of, going offline.
As part of the engagement, our experts will interview your operations staff and security analysts to identify and review:
- Business critical assets
- Asset inventories
- Architecture
- Existing or planned tools
Deliverables
Cylance Consulting helps your organization develop a security monitoring plan that includes:
- Architectural changes
- Network sensor locations
- Log collection methods
- Processes and procedures
Organizations must be proactive and vigilant in safeguarding critical infrastructure from cyber risk. Contact Cylance Consulting or your technology provider to learn more about ICS security monitoring.
Download the Cylance ICS Security Monitoring Datasheet (.PDF)
ICS Security Fundamentals:
Assistance To Secure Mission-Critical Infrastructure
Industrial Control Systems (ICS) often perform functions to operate critical infrastructures in industries such as electric, water and wastewater, oil and natural gas, transportation, chemical, and other manufacturing industries. As control systems adopt IT solutions to enable connectivity with business systems and remote access, they have begun to resemble traditional IT systems with the same security risks.
ICS Security Fundamentals provides the opportunity for the client to work with Cylance Consulting’s ICS security experts to implement security best practices in these challenging environments.
Benefits
- Increase comprehension of cybersecurity in industrial control systems
- Understand potential threat vectors in ICS and learn ideas for securing systems
- Identify areas of strength and best practices being followed within the organization
- Improve the organization’s risk management and decision-making process
Service Overview
Whether your organization needs assistance reviewing a design, selecting a vendor, or building a validation plan, our dedicated team of ICS professionals is here to share their varied knowledge and experience to evaluate and manage risk in your critical infrastructure. Our services include, but are not limited to:
- Security Standards Review
- Security Design Review
- Security Technology Review
- Security Testing and Validation Planning or Execution
- Vendor Selection and Specification Assistance
- Security Training
Find out how Cylance Consulting can help you remediate a multitude of issues that may be negatively impacting your critical infrastructure. Contact us or your technology provider today.
Download the Cylance ICS Security Fundamentals Datasheet (.PDF)
ICS Policy Gap Analysis:
Develop a Comprehensive Cybersecurity Policy for Your Critical Infrastructure
The NIST Cybersecurity Framework (CSF) provides a flexible, repeatable, and costeffective risk-based approach to managing information security risk through the analysis of five core functions: identify, protect, detect, respond, and recover. The NIST CSF provides a foundation for developing and maintaining a robust and resilient industrial control system (ICS) posture that is focused on policy, process, and procedures.
Cylance Consulting’s ICS Policy Gap Analysis assists organizations in building a comprehensive cybersecurity policy for control system environments to help minimize exposure to risk and ensure a clear strategy for handling incidents while maintaining a process for continual improvement and monitoring.
Benefits
- Align the organization with industry-recognized best practices
- Leverage the knowledge of our ICS experts as related to NIST CSF, NERC CIP, and other industry requirements
- Identify the shortcomings and resources needed to meet requirements
- Ensure infrastructure, staff, and security controls are robust and resilient
Service Overview
The goal of Cylance Consulting’s ICS Policy Gap Analysis is to evaluate the policies, standards, and procedures implemented by the organization and how they align within NIST CSF’s five core functions. Our ICS experts will work with your staff to identify positive practices in your program as well as areas for improvement.
The analysis includes:
- Collection of policy documents
- Interpretation and analysis
- Determination of degree of alignment with NIST CSF Category and Subcategory
Deliverables
Cylance Consulting provides the organization with a comprehensive report detailing:
- Assessment findings and alignment to the NIST CSF
- Remediation strategies to achieve compliance with the NIST CSF and industry best practices
- Instructions for developing a roadmap for continuous improvement and monitoring
Know if your cybersecurity policy stands up to industry best practices for managing critical infrastructure. Contact Cylance Consulting or your technology provider to discuss your needs.
Download the Cylance ICS Policy Gap Analysis Datasheet (.PDF)

